Information Security Management
We at IIPRD unambiguously understand the importance and criticality of IP and secrecy of client confidentiality data. As an inherent and strongly followed practice, all data submitted by our Clients is implicitly kept and shared strictly on need to know basis and maintained confidential with clear outlined liabilities of accessing members of the firm, with this aspect being viewed as one of the top priorities and critical elements for maintaining a long-term relationship with our clients.
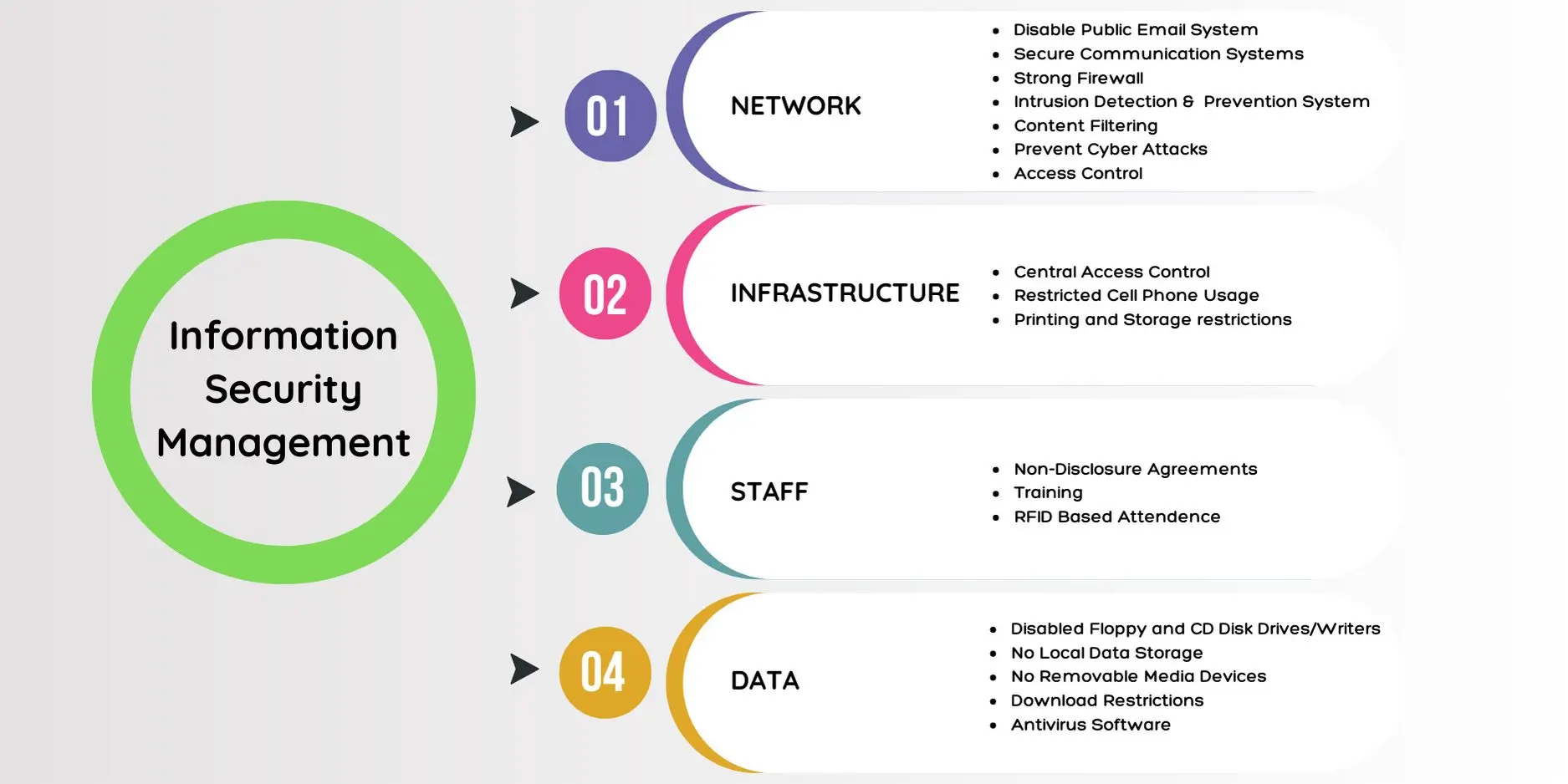
We are committed in protecting our Client’s IP throughout the project cycle and thereafter. IPR protection policy & project confidentiality includes Non-Disclosure Agreements (NDA’s) with clients to ensure security and confidentiality of information, where an NDA is executed with each client and all private information is respected. We also train our staff so that they understand the importance of secrecy and protection of clients’ information. We are committed to adherence of international standards for best practices on information security thereby ensuring Confidentiality, Integrity and Availability of information assets.
In addition to the above, we at IIPRD also implement below exemplary IS Management Practices for strengthening client confidentiality obligations and access controls as an integral part of information security management:
- IIPRD comprehensively implements access controls on need-to-basis, wherein access controls include security mechanisms that ensure only authorized users can access information assets. Few examples of access controls that have been implemented at IIPRD include but are not limited to implementation of passwords, two-factor authentication, biometric identification, and role-based access controls.
- IIPRD has a comprehensive IT Asset Usage and Monitoring Policy that allows it is define the manner in which the assets would be used, accessed, and controlled. IIPRD has defined security implementations in the forms of secured private servers, anti-virus implementations, and firewall installations to do its best to keep the data secured.
- IIPRD periodically conduct security awareness trainings, wherein such trainings are provided by third-party, experienced, and independent trainers to firm members and employees on aspects such as common security threats, phishing, malware, and social engineering. Such trainings also assist employees recognize and avoid these threats, reducing the risk of a security breach.
- IIPRD also actively promotes and incorporates implementation of data encryption. Encryption protects data by transforming it into a code that can only be deciphered by authorized users. By implementing encryption, IIPRD is able to protect sensitive data both in transit and at rest, reducing the risk of data theft or unauthorized access.
- IIPRD regularly undertakes vulnerability assessments that assist in identifying vulnerabilities in the IT infrastructure, and can help identify and remediate vulnerabilities before they can be exploited by attackers.
IIPRD also, on occurrence basis, implements incident response procedures that outline steps that the firm would take in the event of a security incident. By developing and implementing incident response procedures, IIPRD is able to quickly
